
Cybersecurity is one of the biggest issues facing organizations today. The effects of a data breach can be catastrophic - both to reputation and bottom line.
But keeping up with the latest threats and maintaining internal security protocols isn't easy. A lapse by any member of staff can open the door to cyber-criminals.
For some frank, honest and timely advice, we spoke to Tracy Reinhold, Vice President and Chief Security Officer for Everbridge. With responsibility for both digital and physical security, as well as global compliance for the organization, Tracy tackles the cybersecurity challenge head-on every day.
Read on for our Q&A with him, or watch the summary video, where we speak about how organizations can quantify their level of risk, what Information Security Managers should be doing to protect themselves, and why employee security awareness campaigns are so essential.
SnapComms (SC): What are the biggest types of cyber risk that organizations are facing at the moment?
Tracy Reinhold (TR): Great question and unfortunately, the answer is not straightforward. It depends on the organization and the vertical in which you work as to what kind of risk you face. For example, if you're in the retail business, point of sale scams are a huge issue there.
But I think the biggest is the ransomware issue. It’s a huge issue globally, affecting every kind of company you can imagine, and there's no real policy that's universally accepted as to how you address ransomware. It would depend on what your business’ risk appetite is and then whether or not you are comfortable paying ransom.
SC: How can organizations quantify their level of risk?
TR: The threat is more pronounced for companies that have more hands on keyboards. If you are in a rudimentary manufacturing facility that is not automated, it’s a little less scary than if you were on an AI-driven or machine learning platform that allows a company to accelerate production.
The other thing is multiple versions of software operating in a company. When you have this, sending a patch may affect one version but not another, so you're still leaving yourself vulnerable.
So you have to do the reward balancing test. Is the risk worth the reward, what are the revenue drivers, what are the risks that we're going to face as an organization going forward?
Each company should do an honest self-assessment that looks at the vulnerabilities that are present in your system and then what your mitigation plan is to address them.
SC: What things should organizations be doing to help protect themselves?
TR: Part of that is you have to do your basic blocking and tackling. By blocking and tackling what I'm talking about is, are you doing your patching, are you updating your software, are you installing your antivirus software. All of this sounds really straightforward but it's amazing how many companies don't do it.
It's like putting the sign in your front yard that says you have an alarm system, so go to the next house. It's the same thing here. By doing the basics you are making it more difficult for your adversaries or threat actors to access your system.
Asset management is probably the keystone to making sure that your company is protected, because if you don't do that you don't know where your risks are, and it gets exaggerated on a global scale if you're a company that operates in multiple regions.
“It's not if you've been hit, it's when you're going to get hit and how severe it will be.”
Tracy Reinhold - Vice President and Chief Security Officer, Everbridge
SC: What’s been the influence of COVID-19? Do you think it’s exacerbated or created new risks?
TR: It's creating more opportunities for threat actors that's for sure. COVID has accelerated the concept of remote work. In different parts of the world, it was already fairly well established, but it wasn't routine. Now you've got folks using their own devices to dial into the network, so depending on what your capabilities are, what your broadband capabilities are and whether or not the company uses VPN, you may be allowing threat actors to access that way.
The other issue is maintaining the endpoint connections and protecting the endpoints. With remote workers we’re seeing more and more endpoints, so that is a huge cyber risk for the organization.
But in a lot of ways, I think that the pandemic has highlighted vulnerabilities and accelerated the understanding of the cyber warfare space that may not have been understood before. It's sort of a double-edged sword because it did introduce new vulnerabilities, but it also heightened awareness.
At the board level, the C-suite are starting to pay attention, and it allows for better understanding of the cyber capabilities. In the past, one of the challenges has been that the C-suite is very knowledgeable when it comes to the technical aspects, but may not necessarily communicate with the non-technical folks as well.
What this has done is forced that conversation to take place and has forced senior executives to ask questions about where their vulnerability and risks are and what the mitigation plan to address those are for the company, as they move forward.
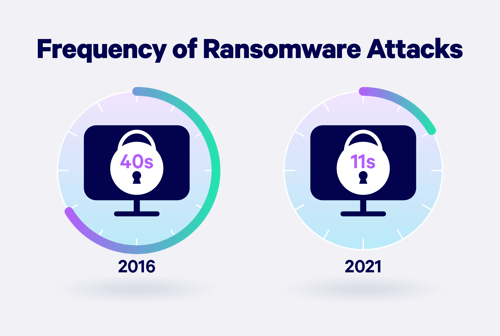
(Source: Embroker)
SC: Are organizations doing enough to protect themselves from cyber threats today?
TR: In business we're on defense all the time, but the bad guys only have to be right once. All they need is one vulnerability that they can exploit.
It goes back to what we talked about earlier, and that is an honest risk assessment, conducted either by the company themselves or through a third party right that has the requisite expertise.
It's not enough to just be preventative; you also have to have a response capability. A lot of that doesn't have to do with the immediate remediation, it has to do with what the public impact is of the breach and how you handle this within the organization.
You need to have a plan in place across the enterprise, detailing how corporate communications are involved and ensuring everybody is sending out a unified message so that you're not confusing your clients, stakeholders or board members.
That’s where most companies suffer the most from a cyber breach. It's not the disruption, it's the impact on how they responded to the disruption, especially if they're a public company.
"With the way that we work today, we seem to mix our personal and our business lives, sometimes on the same machines, which also leads to vulnerability in your private life. That brings in the duty of care or responsibility for an organization. But I find that it's duty to care and not duty of care."
Tracy Reinhold - Vice President and Chief Security Officer, Everbridge
SC: How should companies be building awareness among employees of cyber best practice?
TR: Number one is information security training. A lot of companies don't invest in this. How do you identify phishing, do you know what a phishing email looks like? It's still fairly simple to introduce malware into a company through a phishing expedition. And yet we still fall for it every year, so are you having those types of tests in your organization?
Are you thinking about social engineering? Are you talking to people about, ‘Hey if you're on vacation maybe don't post on instagram until you get back’? Because that also tells your threat actors that you're away from your office, which gives them another viable entry.
One of the classic examples is, if you’re an entry level employee and you're getting a thank you from the CEO on something that is routine. A little light bulb should go off because that's probably not genuine. Hold your cursor over the hyperlink for the email address and see that it's from somebody somebody at gmail – that’s probably not the boss.
Organizations that skimp on information security training pay the cost at the end of the day.
SC: How important are communications in managing the cyber threat?
TR: The speed of communications is so fast that if you don't control the narrative, the narrative will control you. If you don't get ahead of the threat, then you are at the mercy of social media or anybody else who picks it up, and that can really be disruptive to an organization’s stock price and reputation.
There are several examples where companies sat on the breach until they could solve it, but then they lost control of what was said to the public, and we watched their stock price drop exponentially, which also resulted in the removal of CEOs.
Conversely, a company that is breached and then has an aggressive campaign corporate wide, that says we've been a victim of a breach, here's how we're addressing it, here's the implications and here's what we're doing moving forward. Those companies seem to sustain themselves relatively unscathed compared to those that try to massage the message or withhold it.
The ability to push out messages to your own internal stakeholders very quickly is critical. Having templates designed in a system that allows you to send one to your board members, one to the C suite, one to your response team, all at the same time, all with different messages.
Because the board doesn't need to know the level of granularity that your response team knows, but if you keep them in the loop and keep them informed it's less disruptive for your response team, and they can focus on the problem at hand.
SC: What are some of the biggest mistakes that you see companies making with their cyber security protection?
TR: The biggest thing is not doing your basic blocking and tackling. And thinking that it won't happen, that I don't have anything anybody wants. That is so blatantly untrue. Economic espionage and stealing intellectual property is a huge problem.
Being unaware of the risk and unaware of the value of the product that you produce creates an environment of complacency, which then lends itself to intrusion by cyber criminals. If you lose that vigilance, you stop doing the basic stuff that you're supposed to do, and you open up your organization to a potential attack.
The SnapComms platform offers a range of communication tools, pre-built templates and features to help improve your cybersecurity. Contact us to learn more or explore our information security solutions.



